Content Gateway Cert Error
WS1 UEM Content installation Certificate error
In some rare cases (for UAG release 2106 or maybe later) installation Content Gateway on UAG can be failed with messager in logs like this:
13:10:03.127 [main] INFO c.v.enterprise.content.Application - Starting Application v21.06.0 on <UAG-hostname> with PID 18264 (/opt/vmware/content-gateway/content-gateway.jar started by gateway in /opt/vmware/content-gateway)
13:10:03.132 [main] INFO c.v.enterprise.content.Application - No active profile set, falling back to default profiles: default.
13:10:05.159 [main] INFO c.v.enterprise.content.Application - PostConstruct: Application instance created.
13:10:05.850 [main] ERROR c.v.e.c.security.AuthenticatorImpl - **Exception while generating public key from modulus and exponent**
13:10:05.851 [main] WARN o.s.c.a.AnnotationConfigApplicationContext - Exception encountered during context initialization - cancelling refresh attempt: org.springframework.beans.factory.UnsatisfiedDependencyException: Error creating bean with name 'server': Unsatisfied dependency expressed through field 'connectivityAdapter'; nested exception is org.springframework.beans.factory.UnsatisfiedDependencyException: Error creating bean with name 'connectivity': Unsatisfied dependency expressed through field 'authenticator'; nested exception is org.springframework.beans.factory.BeanCreationException: Error creating bean with name 'authenticatorImpl': Invocation of init method failed; nested exception is java.lang.IllegalStateException: java.security.spec.InvalidKeySpecException: java.security.InvalidKeyException:
**RSA keys must be at least 512 bits long**
13:10:05.877 [main] ERROR o.s.boot.SpringApplication - Application startup failed
❗️This artice is only workaround for error and don’t contain deep explanation root cause problem analyze
- If you already upload public certificate to Groups & Settings > All Settings > System > Enterprise Integration > Content Gateway, delete it and save settings
- Option step: upload/update your default UAG certificate for UAG console in TLS Server Certificate Settings pointed it to Internet Interface (more detailed here: Update SSL Server Signed Certificates)
- Enable Content service in Edge Service Settings. It should be started after a couple of minutes with green light. At this stage you may notice URL your content gateway is reacheble, but get TLS/SSL error
- Repopulate your public certificete deleted on Stage 1.
- Disable and Enable Content service in Edge Service Settings to reread settings from API server. After that your Content Gateway URL should work as expected with your public certificate.
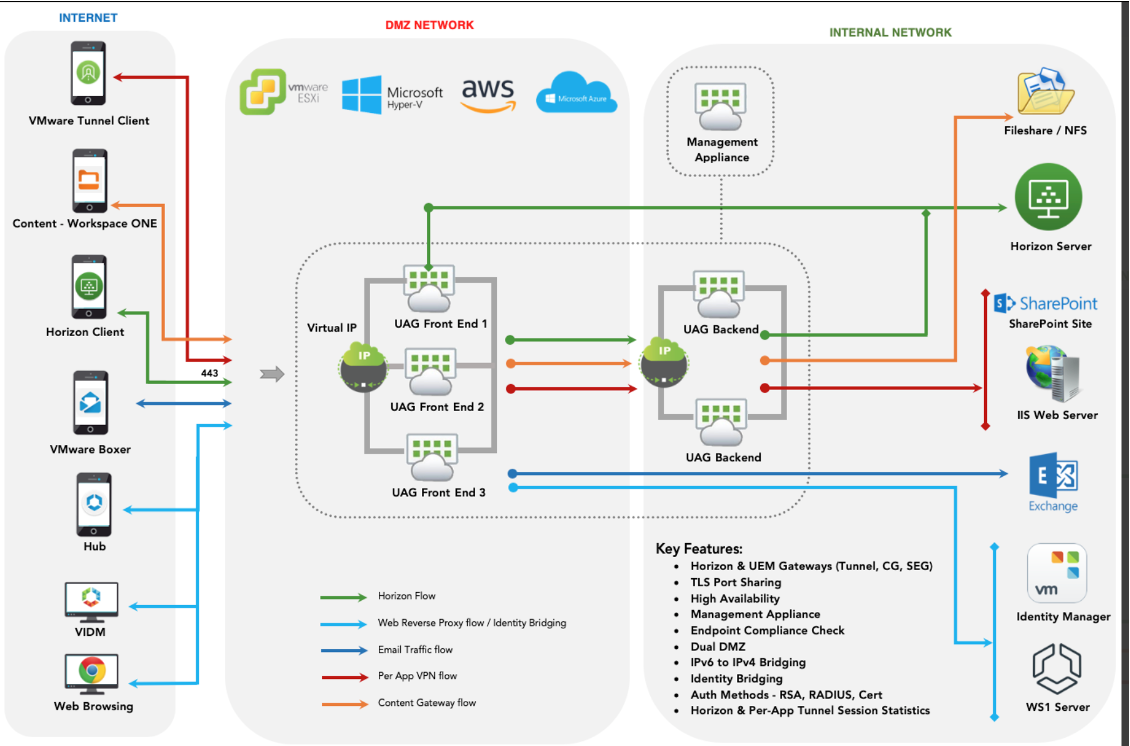
SEG on UAG
UAG Architecture

SEG Architecture
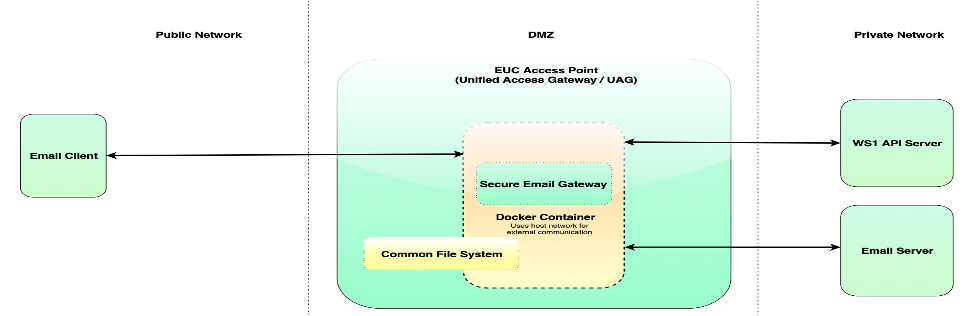

- SEG process running inside the container also behaves as just any other process on UAG, from networking perspective.
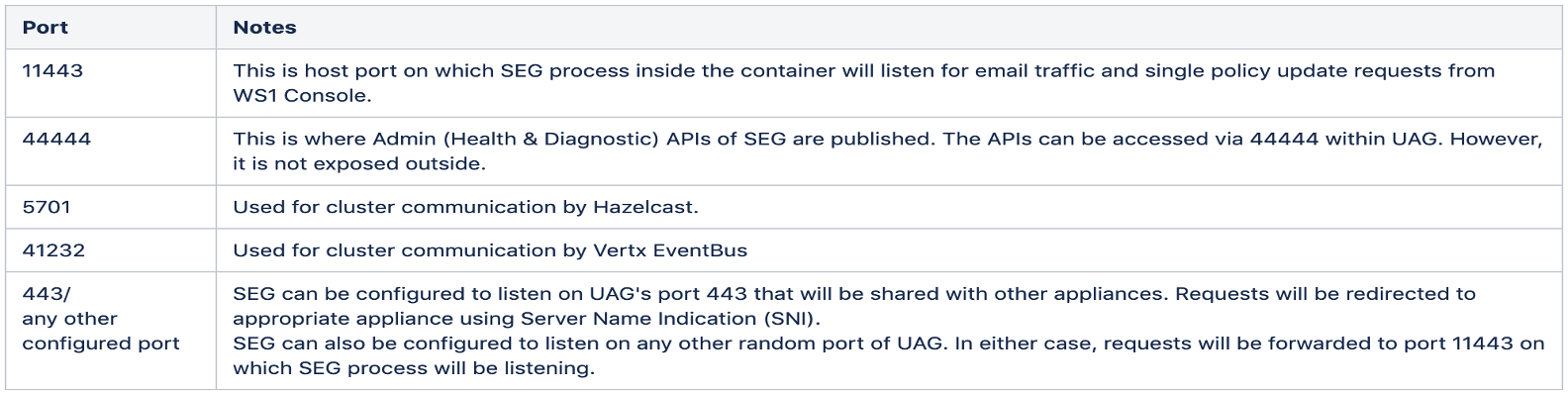
- Handling ports - there is no port mapping between UAG host and the container, as container runs with host network stack itself. There are fixed set of ports reserved on UAG for running SEG. These are listed below:

UAG Admin UI and Logs
- Admin UI: https://UAG IP:9443/admin
- Show Edge service settings.
- Log archive: UAG + All edge services
- Log level settings: UAG logs level only.
Important logs:
- Appliance-agent: Configuration related.
- SEG: SEG service-related.
- Docker: Docker related.
Logs file path:
SEG logs: /var/log/vmware/docker/seg
UAG logs: /opt/vmware/gateway/logs
and /var/log/vmware/appliance-agent/ (Appliance agent logs)
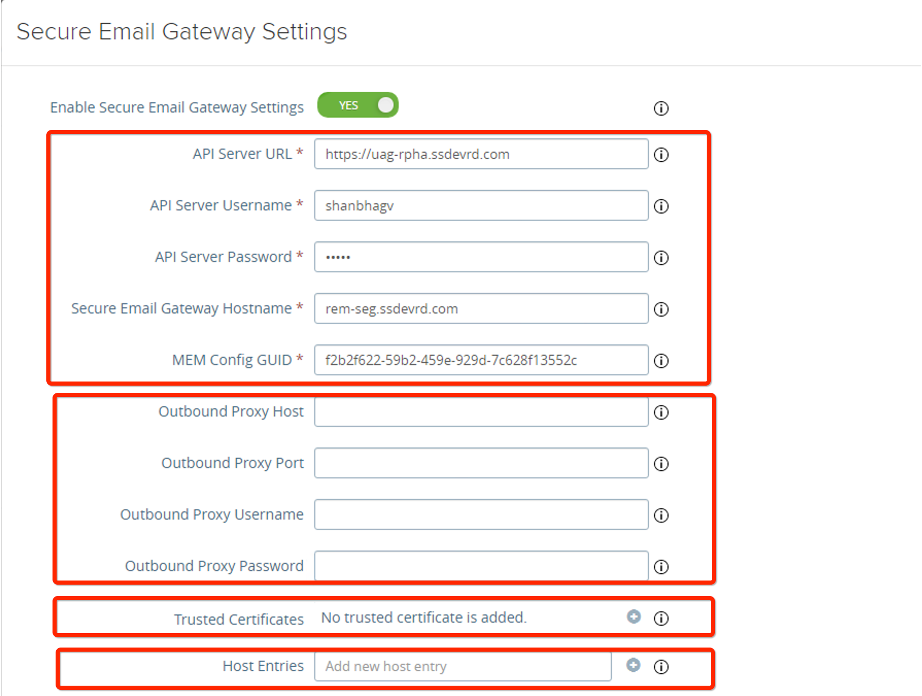
SEG Configuration
- General mem configuration.
- Outbound proxy configuration.
- Trusted certificates.
- Host file entries.
- Add SSL certificate.
- Save (Install and configure)

Troubleshooting SEG
SEG configuration issues
- Check Appliance-agent logs.
- Check v2-seg-installer and app logs (Available inside SEG folder).
- If no SEG folder then check docker logs.
- If docker fails to start, then check Journalctl -xe
SEG application issues
Enable SSH on UAG
- Connect to UAG using vCentre web console
- Navigate cd /opt/vmware/gateway/bin/ and execute ./enable_ssh.sh
Check Docker Status
systemctl status docker.service
docker ps
To check all required service is up and running: netstat –ntlp
Firewall and connection issues - https://docs.vmware.com/en/Unified-Access-Gateway/3.10/com.vmware.uag-310-deploy-config.doc/GUID-390D3A2A-0CB7-4A82-9B0F-D525B74CF55B.html
SSL Offload
##SSL offloading on UAG
SSL offload to external LoadBalancer usually a good practice to improve performance DS’s and UAG servers, avoiding it to extra work with encrypt traffic
Also you should to change public Certificate in one place instead of replace it in each server
Note: all above are valid if you have alot devices registred in WS1 (more than 2000). For smaler deployments usually you may stay at much easy deployment without load balancers.
In case of SSL offloadin you should use one of the scenarios:
- Traffic isn’t encrypted after termination on LoadBalancer


This can be used for traffic to Devcie Services endpoint only.
Even if you setup SSL offload check box during DS installation AWCM endpoint will use encriprion with self-generated certificate for traffic on port 2001. In this case you need to enshure tant LoadBalancer trust for this cert (or ignores SSL errors)
❗️All you internal connection to AWCM must go though LoadBalancer enpoint to proper trust
- Traffic is reencrypted after termination on LoadBalancer with local cert


Despite the availability SSL offload check box in SEG and Content setup in WS1 Console, UAG server can work only with encripted http-traffic.
SEG
The UAG does not support any non-encrypted protocols. Therefore, SEG only supports SSL re-encryption (SSL bridging) or SSL pass through
Content:
HTTP traffic is not allowed for Content Gateway on port 80 on Unified Access Gateway because TCP port 80 is used by the edge Service Manager.





