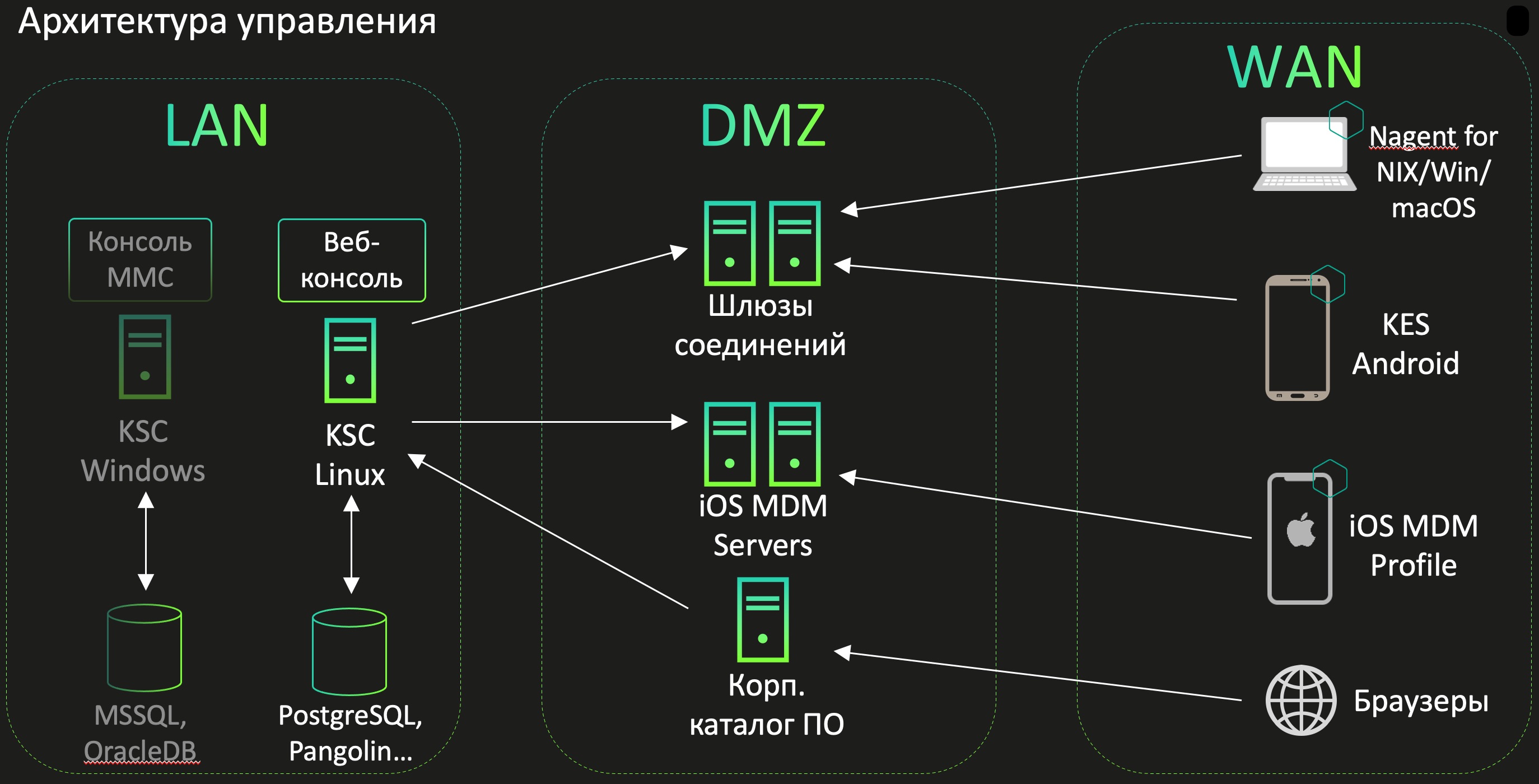
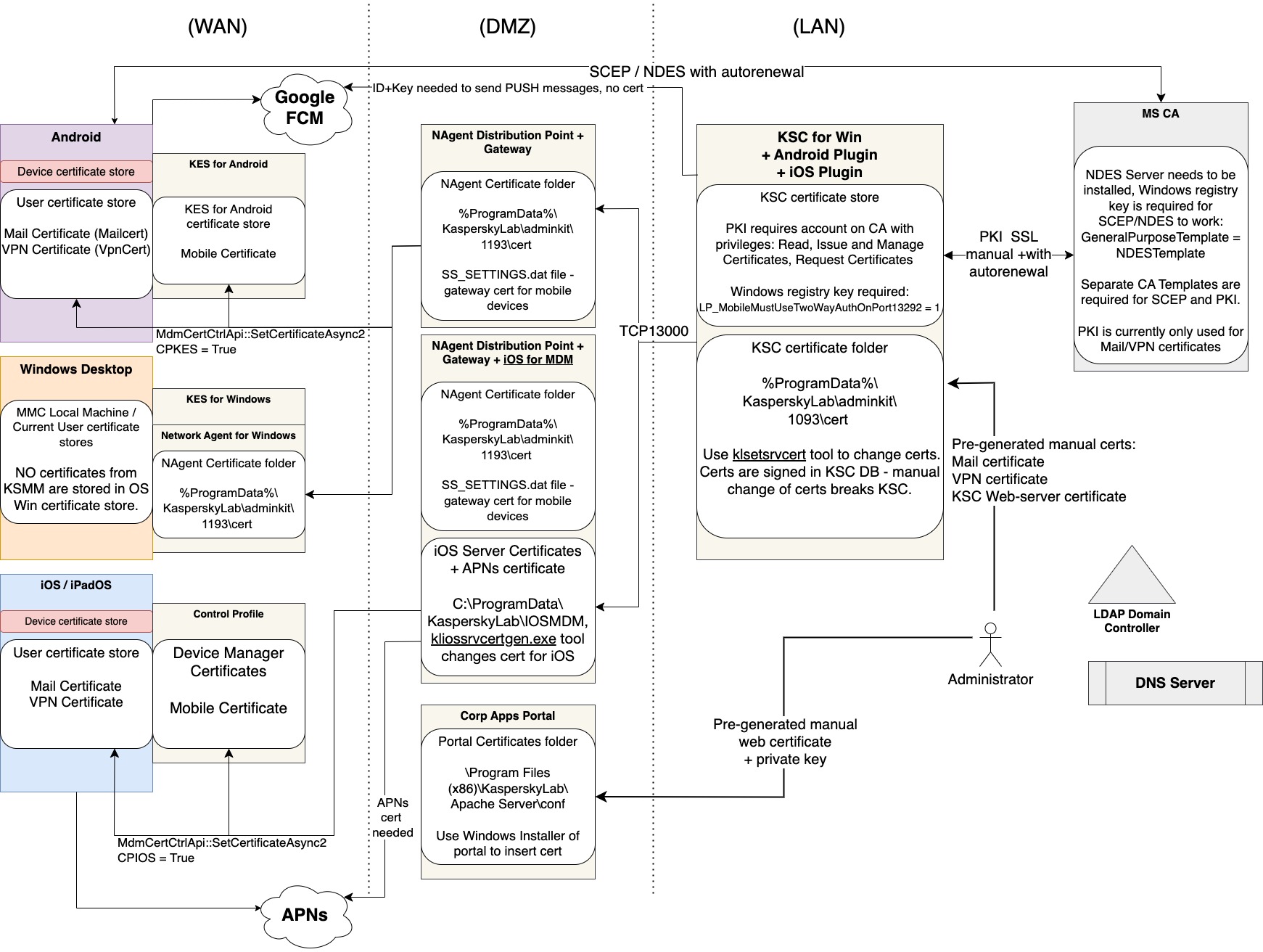
KSMM Windows Desktops
Windows Desktop Management
Desktop management is done using scripts. Scripts are packed into “Installation packs”:
 Entry point for an installation pack is a “.BAT”, “.EXE” or “.MSI/.MSP” file. A BAT-file may be used to launch Powershell, Python or any other type of scripts.
Entry point for an installation pack is a “.BAT”, “.EXE” or “.MSI/.MSP” file. A BAT-file may be used to launch Powershell, Python or any other type of scripts.
Scripts are launched using Scheduled Tasks of Remote App Install type:
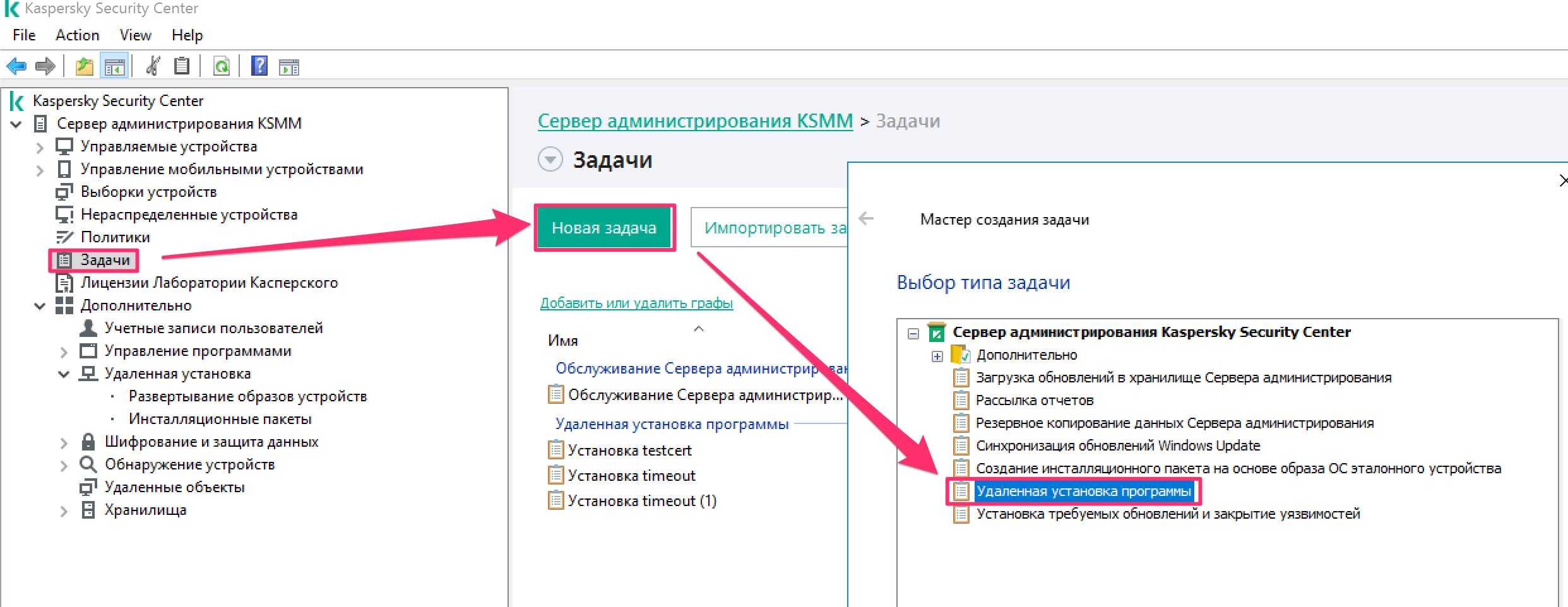

Python script launch
Example of entry-point BAT-file runpy.bat running Python script and then logging a success in a text file:
c:\python3\python.exe testpy.py
@echo SCRIPT RUN SUCCESS>%SYSTEMDRIVE%\LOG.txt
Python testpy.py payload script to create a file needs to be placed in the same installation pack:
if __name__ == "__main__":
text = "File write"
file1 = open("c:\\testFile.txt", "w")
file1.write(text)
file1.close()
Powershell script launch
Example of entry-point BAT-file runps.bat running Powershell script and then logging a success in a text file:
Powershell.exe -executionpolicy remotesigned -File certinstall.ps1
@echo CERT INSTALL SUCCESS>%SYSTEMDRIVE%\LOG.txt
Powershell payload script certinstall.ps1 to decrypt and install a PFX certificate test2.pfx provided in the installation pack in the Windows certificate store (Local Machine store):
$Pass = ConvertTo-SecureString -String '12345' -Force -AsPlainText
$User = "lab\administrator"
$Cred = New-Object -TypeName "System.Management.Automation.PSCredential" -ArgumentList $User, $Pass
Import-PfxCertificate -FilePath test2.pfx -CertStoreLocation Cert:\LocalMachine\My -Password $Cred.Password
Parameters transfer
Parameters can be transferred using the UI, parameter section in the installation pack:
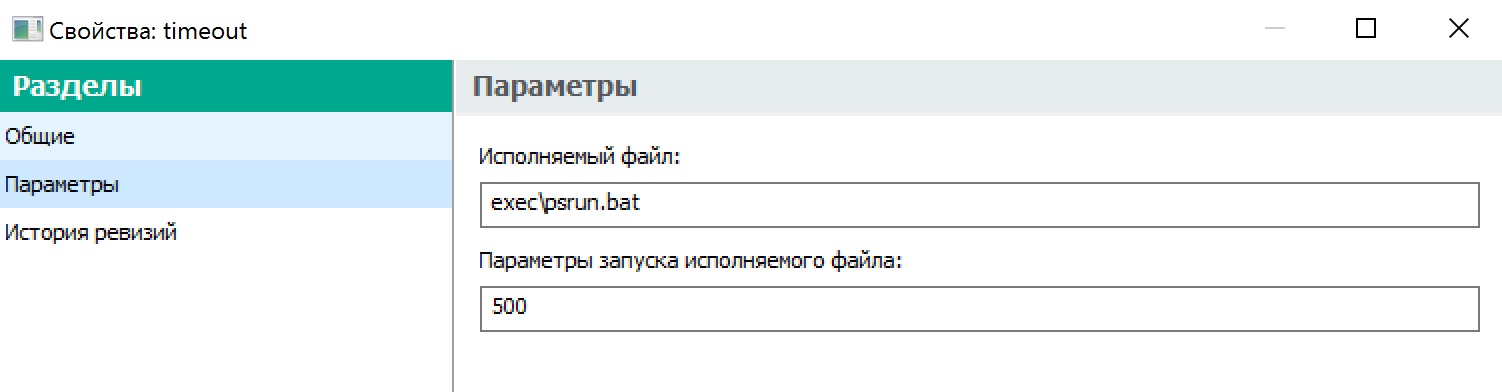
 Parameters are sent to the entry-point file (BAT-file) and should be handled there. Example of the certinstall.bat BAT-file running Powershell and transferring a “seconds” parameter in %1:
Parameters are sent to the entry-point file (BAT-file) and should be handled there. Example of the certinstall.bat BAT-file running Powershell and transferring a “seconds” parameter in %1:
Powershell.exe -executionpolicy remotesigned -File timeout.ps1 -sec %1 > c:\PSLOG.txt
Powershell script payload timeout.ps1 to insert a value of seconds in the Windows registry, for the system to timeout (default of 120sec in case parameter is not provided) and lock screen in case of inactivity (restart needed for registry parameter to be applied):
param([Int32]$sec=120)
Write-Host 'Current timeout value: '
Get-ItemPropertyValue 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System' 'InactivityTimeoutSecs'
Set-ItemProperty -Path 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System' -Name InactivityTimeoutSecs -Value $sec
Write-Host 'New timeout value: '
Get-ItemPropertyValue 'HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System' 'InactivityTimeoutSecs'
Restart-Computer -Force
OpenAPI
Links
Warning
KlAkOAPI Python Package is a wrapper over the regular REST API calls. I do NOT recommend its’ usage, because it does not cover all classes, parameters and attributes available.
Articles
Config / Auth
Access with OpenAPI requires 2 auth elements:
- Local technical user account login/password (Basic Auth method)
- KSC Server certificate verification (optional)
For KSC for Windows, server certificate is located at path:
%ProgramData%\KasperskyLab\adminkit\1093\cert\klserver.cer
Certificate needs to be copied to the machine, from which a script is run.
Login example
REST API Classic login:
import requests
import base64
import json
import urllib3
from pprint import pprint
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
ksc_server = "https://ksmm.demo.local:13299"
url = ksc_server + "/api/v1.0/login"
user = "user_api"
password = "P@ssw0rd"
data = {}
user = base64.b64encode(user.encode('utf-8')).decode("utf-8")
password = base64.b64encode(password.encode('utf-8')).decode("utf-8")
session = requests.Session()
auth_headers = {
'Authorization': 'KSCBasic user="' + user + '", pass="' + password + '", internal="1"',
'Content-Type': 'application/json',
}
response = session.post(url=url, headers=auth_headers, data=data, verify=False)
print(f'Server response = {response.status_code}')
KlAkOAPI Python Package Login:
import socket
import uuid
import datetime
from sys import platform
from KlAkOAPI.Params import KlAkArray, paramBinary, strToBin, dateTimeToStr
from KlAkOAPI.AdmServer import KlAkAdmServer
def GetServer():
server_address = 'ksmm.demo.local'
server_port = 13299
server_url = 'https://' + server_address + ':' + str(server_port)
username = 'user_api'
password = 'P@ssw0rd'
SSLVerifyCert = 'C:\\Lab\\klserver.cer'
server = KlAkAdmServer.Create(server_url, username, password, verify = SSLVerifyCert)
return server
# Call server login function:
server = GetServer()
TLS Ciphers
KSC for Win 14.x
SrvUseStrictSslSettings
Switch the supported versions of TLS and cipher suites is done using SrvUseStrictSslSettings flag:
klscflag -fset -pv ".core/.independent" -s Transport -n SrvUseStrictSslSettings -v <value> -t d
Flag SrvUseStrictSslSettings has values from 0 to 5:
0 - allow all TLS versions and cipher suites;
1 - SSL v2 turned OFF;
2 - SSL v2 + SSL v3 turned OFF;
3 - ONLY TLS v1.2;
4 - ONLY TLS v1.2, and ONLY a group of cipher suites with TLS_RSA_WITH_AES_256_GCM_SHA384 - used by default;
5 - ONLY TLS v1.2 and ONLY a selected group of cipher suites;
Options 0 - 3 are NOT recommended, used for compatibility purposes only.
SrvUseStrictSslSettings = 0
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
x96 SEED-SHA RSA SEED 128 TLS_RSA_WITH_SEED_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
x07 IDEA-CBC-SHA RSA IDEA 128 TLS_RSA_WITH_IDEA_CBC_SHA
TLS 1.1
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
x96 SEED-SHA RSA SEED 128 TLS_RSA_WITH_SEED_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
x07 IDEA-CBC-SHA RSA IDEA 128 TLS_RSA_WITH_IDEA_CBC_SHA
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 521 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 521 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
xc077 ECDHE-RSA-CAMELLIA256-SHA384 ECDH 521 Camellia 256 TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
xc0a1 AES256-CCM8 RSA AESCCM8 256 TLS_RSA_WITH_AES_256_CCM_8
xc09d AES256-CCM RSA AESCCM 256 TLS_RSA_WITH_AES_256_CCM
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc0 CAMELLIA256-SHA256 RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc051 ARIA256-GCM-SHA384 RSA ARIAGCM 256 TLS_RSA_WITH_ARIA_256_GCM_SHA384
xc061 ECDHE-ARIA256-GCM-SHA384 ECDH 521 ARIAGCM 256 TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 521 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
xc0a0 AES128-CCM8 RSA AESCCM8 128 TLS_RSA_WITH_AES_128_CCM_8
xc09c AES128-CCM RSA AESCCM 128 TLS_RSA_WITH_AES_128_CCM
xc076 ECDHE-RSA-CAMELLIA128-SHA256 ECDH 521 Camellia 128 TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
xba CAMELLIA128-SHA256 RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256
x96 SEED-SHA RSA SEED 128 TLS_RSA_WITH_SEED_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
xc050 ARIA128-GCM-SHA256 RSA ARIAGCM 128 TLS_RSA_WITH_ARIA_128_GCM_SHA256
xc060 ECDHE-ARIA128-GCM-SHA256 ECDH 521 ARIAGCM 128 TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256
SrvUseStrictSslSettings = 1
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
TLS 1.1
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 521 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 521 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 521 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 521 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 521 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
SrvUseStrictSslSettings = 2
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS 1.1
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 253 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
xc077 ECDHE-RSA-CAMELLIA256-SHA384 ECDH 256 Camellia 256 TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
xc0a1 AES256-CCM8 RSA AESCCM8 256 TLS_RSA_WITH_AES_256_CCM_8
xc09d AES256-CCM RSA AESCCM 256 TLS_RSA_WITH_AES_256_CCM
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc0 CAMELLIA256-SHA256 RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc051 ARIA256-GCM-SHA384 RSA ARIAGCM 256 TLS_RSA_WITH_ARIA_256_GCM_SHA384
xc061 ECDHE-ARIA256-GCM-SHA384 ECDH 253 ARIAGCM 256 TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
xc0a0 AES128-CCM8 RSA AESCCM8 128 TLS_RSA_WITH_AES_128_CCM_8
xc09c AES128-CCM RSA AESCCM 128 TLS_RSA_WITH_AES_128_CCM
xc076 ECDHE-RSA-CAMELLIA128-SHA256 ECDH 256 Camellia 128 TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
xba CAMELLIA128-SHA256 RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
xc050 ARIA128-GCM-SHA256 RSA ARIAGCM 128 TLS_RSA_WITH_ARIA_128_GCM_SHA256
xc060 ECDHE-ARIA128-GCM-SHA256 ECDH 253 ARIAGCM 128 TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256
SrvUseStrictSslSettings = 3
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 253 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
xc077 ECDHE-RSA-CAMELLIA256-SHA384 ECDH 256 Camellia 256 TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
xc0a1 AES256-CCM8 RSA AESCCM8 256 TLS_RSA_WITH_AES_256_CCM_8
xc09d AES256-CCM RSA AESCCM 256 TLS_RSA_WITH_AES_256_CCM
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc0 CAMELLIA256-SHA256 RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256
x84 CAMELLIA256-SHA RSA Camellia 256 TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
xc051 ARIA256-GCM-SHA384 RSA ARIAGCM 256 TLS_RSA_WITH_ARIA_256_GCM_SHA384
xc061 ECDHE-ARIA256-GCM-SHA384 ECDH 253 ARIAGCM 256 TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
xc0a0 AES128-CCM8 RSA AESCCM8 128 TLS_RSA_WITH_AES_128_CCM_8
xc09c AES128-CCM RSA AESCCM 128 TLS_RSA_WITH_AES_128_CCM
xc076 ECDHE-RSA-CAMELLIA128-SHA256 ECDH 256 Camellia 128 TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
xba CAMELLIA128-SHA256 RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256
x41 CAMELLIA128-SHA RSA Camellia 128 TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
xc050 ARIA128-GCM-SHA256 RSA ARIAGCM 128 TLS_RSA_WITH_ARIA_128_GCM_SHA256
xc060 ECDHE-ARIA128-GCM-SHA256 ECDH 253 ARIAGCM 128 TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256
SrvUseStrictSslSettings = 4 (default)
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 256 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
SrvUseStrictSslSettings = 5
| Hexcode | Cipher Suite Name (OpenSSL) | KeyExch Encryption Bits | Cipher Suite Name |(IANA/RFC) |
TLS 1.2
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xcca8 ECDHE-RSA-CHACHA20-POLY1305 ECDH 256 ChaCha20 256 TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256