IIS Hardening
Device Services IIS
Disable insecure TLS/SSL protocol support
- Yes, you can disable this and this will not have any impact on AirWatch Applications because we have made the necessary changes in our components as well.
POODLE attack, SSLv3 etc have been taken care by our developers in console version 8.1 and above.
Remove the default page or stop/disable the IIS server
- Yes, you can remove the default page, but do not disable the IIS server. Recommended not to disable the IIS server.
Disable TLS/SSL support for RC4 ciphers
- Please refer the below link for disabling RC4 cipher.
https://support.microsoft.com/en-us/kb/245030
https://support.microsoft.com/en-us/kb/2868725
Disable SSLv2, SSLv3, and TLS 1.0
- This will not have any impact on the AirWatch application and you can have this disabled. Best solution for this will be to enable TLS1.2
https://support.microsoft.com/en-us/kb/187498
Regarding Ciphers suites
- Be it any kind of Ciphers(Static key cipher, 3DES cipher, Strong cipher) the best solution for this is to enable TLS. Also, the MicrosoftKB article 245030 as mentioned in the ticket is the best solution for all the Cipher questions.
https://support.microsoft.com/en-us/kb/245030
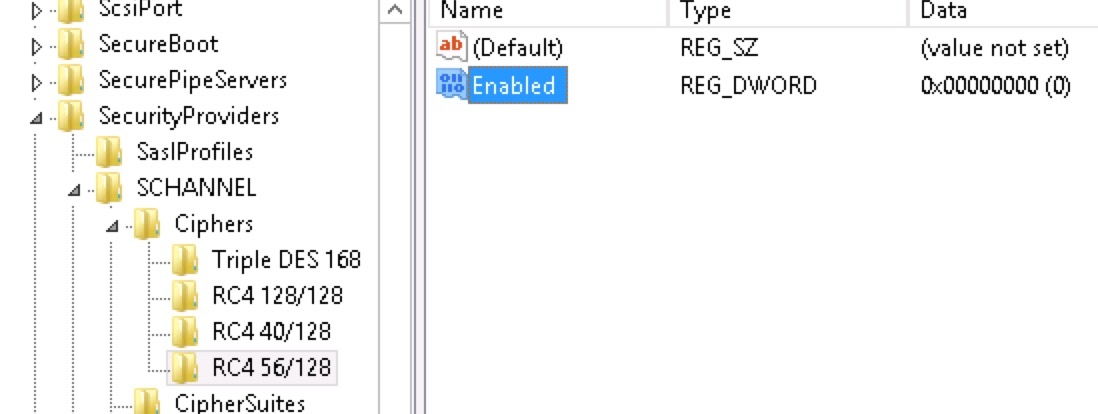
The RC4 cipher can be completely disabled on Windows platforms by setting the “Enabled” (REG_DWORD) entry to value 00000000 in the following registry locations:
• HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128
• HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128
• HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128
Disabling SSL and enabling TLS is out of Airwatch’s scope as you have to make registry changes locally on the server:
Disabling SSL 3.0- https://www.digicert.com/ssl-support/iis-disabling-ssl-v3.htm
Enabling TLS - https://support.quovadisglobal.com/KB/a433/how-to-enable-tls-12-on-windows-server-2008-r2.aspx
https://www.hass.de/content/setup-your-iis-ssl-perfect-forward-secrecy-and-tls-12
Disabling RC4 on Java:
http://stackoverflow.com/questions/18589761/restict-cipher-suites-on-jre-level
Example:
jdk.certpath.disabledAlgorithms=MD2
jdk.tls.disabledAlgorithms=MD5, SHA1, RC4, RSA keySize < 1024We can either do it at a JRE system wide level or at a JVM instance (such as AWCM) level adding RC4 as a disabled algorithm when a choice has to be made as part of SSL handshake.
In the latter case, It will be a config change on AWCM Service parameters (only change being the added restriction option in $AWCM_HOME/service/AWCMService.exe.parameters).
Tip
IIS Crypto Tool can be used to turn off weak ciphers in Windows Server 2008+
Warning
Usage of iiscrypto tool to disable Cipher Suites, as well as registry keys can break communication between AirWatch components.
Use with extreme caution, ONLY AFTER AirWatch was deployed and tested to be working. Disable Cipher Suites one by one and re-test AirWatch functionality after each change!
Security scanner sees IIS vulnerabilities:
- SWEET32
- POODLE
- TLS_FALLBACK_SCSV
Hardening:
-
POODLE - need to disable SSL 3.0 protocol. Open registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocolsand create keysSSL 3.0\Server (if not created previously), create a DWORD value Enabled = 0;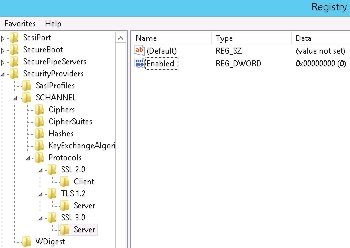

-
SWEET32 - need to disable weak ciphers. Open registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\Triple DES 168, create a DWORD value Enabled = 0. Create keys “RC4 56/128”, “RC4 40/128”, “RC4 128/128” create a DWORD value in all keys called Enabled = 0;
Warning
When turning off Triple DES the RDP protocol to server may stop working. Need to patch RDP to use modern ciphers to solve this problem.
- TLS_FALLBACK_SCSV (only for Windows 2003-2008! see KB from Microsoft: https://support.microsoft.com/kb/980436/en-us) - Open registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNELand create DWORD called UseScsvForTls with parameters:- UseScsvForTls = 0 # Client sends Renegotiation Info extension for TLS protocol
- UseScsvForTls = 1 # Client sends SCSV for TLS protocol - use this to solve problem
Warning
AirWatch Self-Service portal uses TLS1.0/RC4-type cryptography, and gives Error and blank page after IIS hardening!
iOS 11 & Wi-Fi TLS 1.2 Requirements
With the release of iOS 11, TLS 1.2 will now be the default for EAP-TLS negotiation. This may cause an issue with older clients that still need to connect on TLS 1.0 or 1.1. Apple has allowed for a method to override this default setting with a configuration profile sent down to the device via MDM. In order to ensure your iOS devices maintain Wi-Fi connection when upgrading to iOS 11, please follow the steps below:
Note: If you already have a successfully deployed iOS Wi-Fi with EAP-TLS configured, skip to step 3.
- Create a new profile with a Wi-Fi payload using EAP-TLS and General payload configured.
- Ensure that the profile successfully configures Wi-Fi on an iOS device.
- From your profile list view, select the Wi-Fi with EAP-TLS created profile and choose to view XML.
- Export or copy the XML of the profile.
- Edit the XML to remove everything prior to the first
and after its corresponding . - Edit the XML again to add the following bolded key/values (accepted values are 1.0, 1.1, and 1.2). These should be a part of the EAPClientConfiguration key
<key>EAPClientConfiguration</key>
<dict>
<key>AcceptEAPTypes</key>
<array>
<integer>13</integer>
</array>
<key>TLSMaximumVersion</key>
<string>1.1</string>
<key>TLSMinimumVersion</key>
<string>1.0</string>
</dict>- Edit the XML a final time to create a unique identifier for the payload. Locate the PayloadUUID key and edit the values that correspond to the ‘X’s to random values. Please ensure these values are as random as possible to avoid issues with duplicate identifiers (e.g. 123456, 111111, 101010).
<key>PayloadUUID</key>
<string>352B3FD9-B875-45C5-AA0E-AAFEE3XXXXXX</string>- Create another new profile and configure the General payload
- Paste your edited XML into the Custom Settings payload and publish to devices
IISCrypto config from AirWatch
iOS supports all latest ciphers and encryptions – however there are questions with Android, so Android 4.4 will be the baseline.
Protocols: SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1 can be turned off as all of the platforms supports newer protocols.
Warning
Test results at client site (AirWatch ver. 9.2.3): disabling TLS 1.0 showed 4 services failing at AirWatch Device Services Server role - proceed with caution!
VMware Assist
External link: https://stackoverflow.com/questions/52212866/how-can-i-disable-tls-rsa-with-aes-128-cbc-sha-without-disabling-others-as-well
Hardening Assist is basically hardening of Java, disabling TLS_RSA_WITH_AES… in it. Delete RSA Keysize, and add specific protocols.