Software Distribution
External Links
- IE CSP - https://code.vmware.com/samples/3328/windows-10—internet-explorer-csp?h=Airwatch
- MS ADMX templates - https://docs.microsoft.com/en-us/windows/client-management/mdm/understanding-admx-backed-policies
- MS ADMX Group Policy Syntax - https://technet.microsoft.com/en-us/library/cc753471(v=ws.10).aspx
This feature is available through the Apps & Books section. The article also suggests ways to get the executable commands to enter for your Win32 applications in the AirWatch Console. It ends with steps to troubleshoot issues.
Validated Use Cases
AirWatch validated the success of the software distribution feature in the listed use cases. Review the list and see if your deployment is similar to the validated use cases.
- Silent deployment of MSI applications
- MSIs with multiple transforms, and the ability to deploy different transforms to different sets of users
- 64 and 32 bit apps on 64 bit devices
- Installers with registry validations and file checks after installation
- Patch applied to an already deployed application
- Application installation on system context and user context
- A complete silent application installation
- Application installation with dependencies
- Packages with scripts that invoke multiple files (ZIP files that contain PowerShell scripts, EXE, and MST)
- Installation of applications that require reboot
- Applications with disk space, battery, and RAM checks
- Uninstallation of installed applications
Application-specific templates
Internet Explorer
External link - Internet Explorer CSP Documentation
To deploy this sample, navigate to Devices & User > Profile > Add > Windows > Desktop > Device > Custom Settings, then copy and paste the SyncML into the box and publish the profile.
- Modify the values inside of the data tags.
- Change the target of the policies to either device or user. Inside of you will want to change to either ./Device/ or ./User/ but be careful as some policies support User, Device, or Both.
Google Chrome
Deploy attached Chrome CSPs samples via AirWatch. To deploy navigate to Devices & User > Profile > Add > Windows > Desktop > Device > Custom Settings, then copy and paste the SyncML into the box and publish the profile.
- Modify the values inside of the data tags.
- Change the target of the policies to either device or user. Inside of you will want to change to either ./Device/ or ./User/ but be careful as some policies support User, Device, or Both, you can reference which are support by looking at the Chrome ADMX template.
Tips to Get Configurations
Review some ways to get the commands and criteria for the Win32 application. Enter the data in the AirWatch Console when you upload the Win32 application package.
Get the Install Command
Review a few ways to get install commands for Win32 applications.
Note: If an install command prompts for user interaction on the UI, then enter these commands with the User option in the Install Context option.
- Call any script from the command-line that results in a successful installation of the Win32 application.
- The MSI file has the install command pre-populated with silent parameters. You can edit and update these in the AirWatch Console.
- If the EXE or ZIP file contains the MSI file of the Win32 application, use the msiexec command to install.
Get the Uninstall Command
Review some ways to get uninstall command for Win32 applications.
- In a command-line session, use the /? or /help parameters to display supported actions. For example, Mysampleapp.exe /?.
- Look at the HKEYs in the listed registries on the device.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall
- HKCU\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\
- If the EXE contains an underlying MSI, use the msiexec uninstall command. For example, msiexec /x <path_to_file>.
Get Detection Criteria
Use detection criteria to determine if the Win32 application is on devices. To get the detection criteria, install the application and identify the checks on the device.
-
Product ID check
- Run the wmic command and use WMIC Product where name=”
” . - Look at the HKEYs in the listed registries on the device for the product ID.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall
- HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall
- HKCU\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\
- Run the wmic command and use WMIC Product where name=”
-
File check
- Look at the HKEYs listed for Product ID check to find the file criteria.
- Look in the Program Files folder or the Program Files(X86) folder to find the file criteria.
-
Registry check
-
Look at the HKEYs listed for Product ID check to find registries.
-
Look in HKEY_CLASSES_ROOT\Installer\Products.
Get Exit Codes
Use the environmental variable, %errorlevel%, to get exit codes. Use it in conjunction with built-in DOS commands like ECHO, IF, and SET to preserve the existing value of %errorlevel%.
- In a command-line session, run the install command for the Win32 application.
- Run ECHO %errorlevel%.
- The %errorlevel% variable returns the reboot exit code, if the Win32 application requires a reboot for installation.
Troubleshoot Software Distribution Issues
Win32 application installations involve the successful execution of multiple steps. If your application installation fails, follow the troubleshooting steps to find the issue.
Win32 Package Received Reported by App Deployment Agent
The App Deployment Agent on the user’s device handles Win32 application installations. The system deploys the agent to devices either upon enrollment or when it collects the latest App List sample from devices that are already enrolled.
The system holds the app-install commands in the queue until the agent reports back that the application installed.
Steps
Check the following components to see that the agent installed on your end-users’ devices.
- In the AirWatch Console, check that the device successfully enrolled and syncs with the console.
- Check the registry for the AW App Deployment Agent.
- Open a command-line session and run regedit. This opens the Registry Editor.
- In the Registry Editor, go to HKEY_LOCAL_MACHINE > SOFTWARE > Microsoft > EnterpriseDesktopAppManagement.
- Look for the AW App Deployment Agent. The correct status value for the AW App Deployment Agent is 70.
- Check services on the device to ensure that the AW App Deployment Agent is running.
- Check the registry for the AW MDM nodes.
- Open a command-line session and run regedit. This opens the Registry Editor.
- In the Registry Editor, go to HKEY_LOCAL_MACHINE > SOFTWARE > AirWatchMDM > AppDeploymentAgent.
- Find three nodes. If these three nodes are missing, then the device did not receive the Win32 application package.
- App Manifest – This node contains information about the options set in the AirWatch Console on the Deployment Options tab.
- Content Manifest – This node contains information about the options set in the AirWatch Console on the Files tab.
- Queue – This node contains detailed logs about the installation of the application. You can view the logs to check the progress of the download of the application.
Win32 Application Installation Status
After the agent installs on devices, you can track the application installation to troubleshoot issues. The install status for the Win32 application displays the listed statuses.
- Install command ready for device – The install command is queued on the device but the device has not checked in to the AirWatch system.
- Install command dispatched – The device checks in to the system and consumes the install command.
- Installing – The Win32 application is downloading and the installation is in progress on the device.
- Installed – The installation is complete and the device sent an alert to the AirWatch Console.
Status Codes
Steps
If the installation fails after status #2, Install command dispatched, take these steps to find the reason for the failure.
- In the AirWatch Console, validate the configurations for the Win32 application on the Deployment Options tab.
- Go to Apps & Books > List View > Internal and edit the Win32 application.
- Select Edit > Deployment Options tab.
- In the How To Install section, review the Install Context configurations for Device or User.
- Review the Admin Privileges setting.
- Review the Install Command setting.
- Side-load the application to the device to see if this actions triggers the install command.
- In the AirWatch Console, look at the Console Event Logs to find the reason for the failure in HUB > Reports & Analytics > Events > Console Events.
- Look for a failure reason on the device.
- On the device, open a command-line session and run regedit. This opens the Registry Editor.
- In the Registry Editor, go to HKEY_LOCAL_MACHINE > SOFTWARE > AirWatchMDM > AppDeploymentAgent.
- Look in the Queue node at the log field.
- If there is no Queue node, look for a node with the device or user SID. This value has the Win32 application product code. Select the product code to view the reason for installation failure.
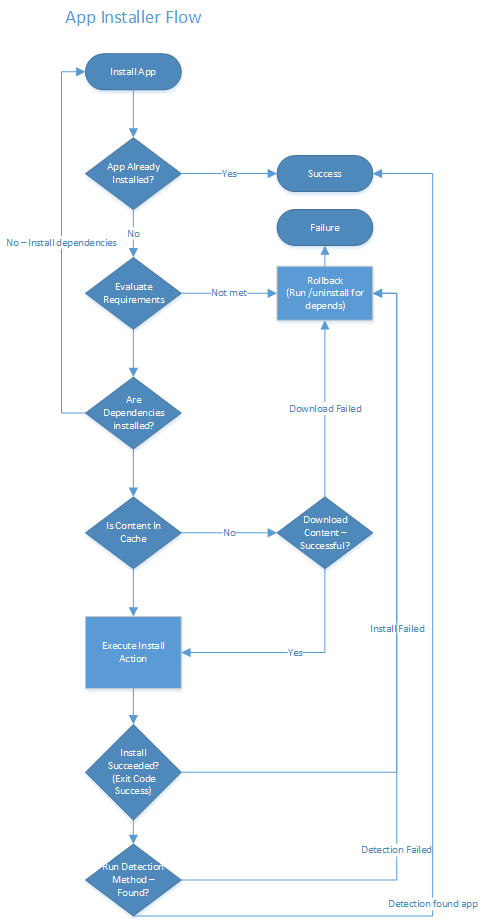
Review the App Installer Flow chart for a depiction of how the device validates the pre and post installation checks.